Think of your software development process like a manufacturing line. Each step, from writing code to testing, packaging, and releasing, is part of a carefully designed system. If at least one batch of raw materials becomes defective during that process, then its final product reaches the consumer; it has incurred enormous costs of recall, repairs, and damage to reputation.
Similarly, if defects in the source code or third-party components occur after deployment, the fallout they cause on security, compliance, and customer trust can be grave. This serves to explain why it is essential to detect issues early in the CI/CD pipeline; basically, it does like automated quality checks at every stage of the production line.
Today, we are going to delve into understanding what DevOps vulnerability scanning in CI/CD is, the reason or importance of having it, its operation, the different types of scans available in the DevOps world, plus the advantage that it offers.
The DevOps lifecycle is usually described as:
Plan → Code → Build → Test → Release → Deploy → Operate → Monitor → Improve.
Security should weave through each stage, ensuring safe delivery at every step.
The question is what DevOps is and its vulnerability scanning CI/CD.
At its core, DevOps vulnerability scanning CI/CD means building security into the same system that developers already use to test and deliver software.
By adding vulnerability scanning into this process, you’re making sure every aspect is safe before the software reaches the customer.
Here’s why security checks can’t be skipped in today’s fast-moving world:
Research shows that 96% of codebases contain open-source software. That means even if your team writes great code, vulnerabilities can sneak in through third-party components.
DevOps encourages frequent releases. Without automated scanning, issues could reach customers much faster than before.
It’s easier and less costly to correct a mistake during development than after it goes live.
Many industries require proof of ongoing security checks to meet standards like PCI DSS or HIPAA.
Studies show the average time to fix high-risk vulnerabilities is about 74 days, that’s over two months of exposure if you don’t have automation helping you.
Let’s keep this simple.
When a developer submits new code, the pipeline automatically starts running tests. Alongside the usual “Does the app work?” checks, security scans run in the background:
If something looks dangerous, like a known weakness in a library, the system flags it. Developers get feedback right away, not weeks later. If it’s a serious problem, the system can stop the release before it reaches customers.
It’s like having a food inspector stationed at every checkpoint in a bakery.
There’s no single scan that covers everything. Different scans look at different features:
Together, these give a full picture of where risks might appear.
So, why invest in this? Here are the real-world benefits teams notice:
Not every tool is created equal. When choosing CI/CD Security Tools, look for:
Even with the best tools, it’s not just about finding problems, it’s about managing them:
This approach is what people mean when they say Vulnerability Management and DevSecOps with CI/CD. It’s about blending security into the daily rhythm of development, not treating it as an afterthought.
To understand how this works in practice, let’s imagine a mobile banking app.
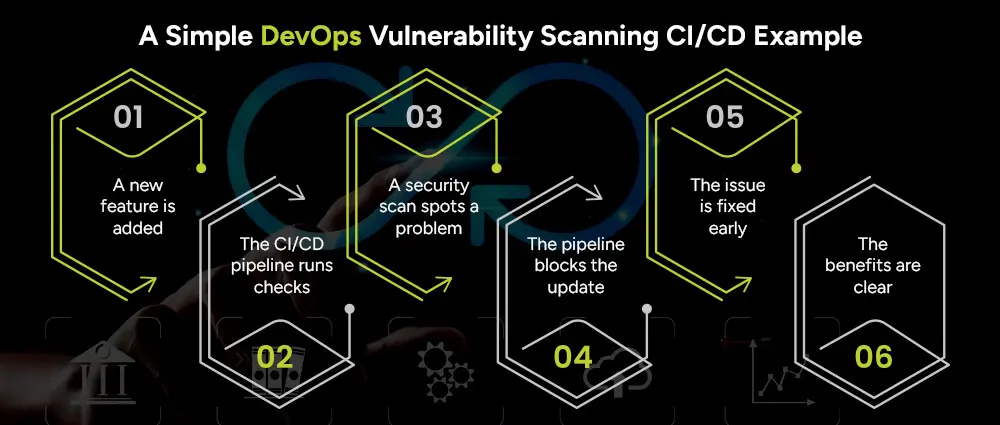
A developer introduces a new feature, such as fingerprint login, to improve user convenience.
As soon as the code is submitted, the CI/CD pipeline automatically runs its usual checks to make sure everything works as expected.
During these checks, a security scan detects that one of the open-source libraries being used has a known vulnerability.
Instead of letting the risky code move forward, the pipeline stops the update until the library is either updated or replaced with a safe version.
Because the problem is caught right away, the issue is resolved before the app is pushed out to thousands of customers.
This simple example shows how early scanning saves embarrassment, prevents financial losses, and protects the trust of users.
Even with the best intentions, teams sometimes make mistakes when adding vulnerability scanning to their CI/CD pipeline. Here are the most common ones:
Teams often add multiple tools right away, which creates confusion and slows progress. It’s better to start small and gradually scale up, whether you’re a small startup using business intelligence tools or a large enterprise experimenting with new tools.
If every small issue blocks progress, developers get frustrated. A good approach is to begin with warnings and only enforce strict rules once the team is comfortable.
Many teams focus only on the app’s code and forget about cloud or infrastructure settings. These are often the weakest points, so scanning them is just as important.
Sometimes vulnerabilities are logged but never assigned to a person. This means they sit unresolved. To avoid this, make sure each issue has a clear owner.
Implementing DevOps vulnerability scanning in a CI/CD pipeline isn’t about slowing things down; it’s about speeding them up safely. By adding lightweight, automated checks into the development process, DevOps development teams like those at Arpatech can ship with confidence, protect users, and avoid costly surprises.
The key takeaway: Treat security like quality as it’s the trend of DevOps as a service, so we need to build security into the recipe, not the cleanup.
CI/CD stands for Continuous Integration and Continuous Delivery or Deployment.
That is how CI/CD forms the assembly line for modern-day software development.
In a broad sense:
The goal is a high automation quotient, whereby the pipeline can manage such repetitive check-ups and human effort can be focused on solving real problems.