Security threats in large organizations have been a big concern in recent years. Cybersecurity risks are no longer just an IT problem, they’re a business-wide issue. Large organizations have a lot to lose, whether it’s a data breach, ransomware attack, or internal misuse of sensitive information. That’s where a cybersecurity risk assessment comes into play.
So, let’s dive into what a cybersecurity risk assessment is, why it’s important, and how you can perform one effectively in a large organization.
Cybersecurity risk assessment refers to a method of identifying, evaluating, and prioritizing cyber threats and vulnerabilities that can adversely affect the organization and its information systems and operations.
Quite simply, it is an audit of all the doors and windows of a digital house. Organizations need to check if they are locked and identify the ones more prone to a burglar’s attention.
You might be thinking, Why go through the hassle? Here’s why:
A great example is seen in Cybersecurity Solutions for healthcare, where assessments help safeguard patient data and meet HIPAA standards.
When done right, a cybersecurity risk assessment offers major wins:
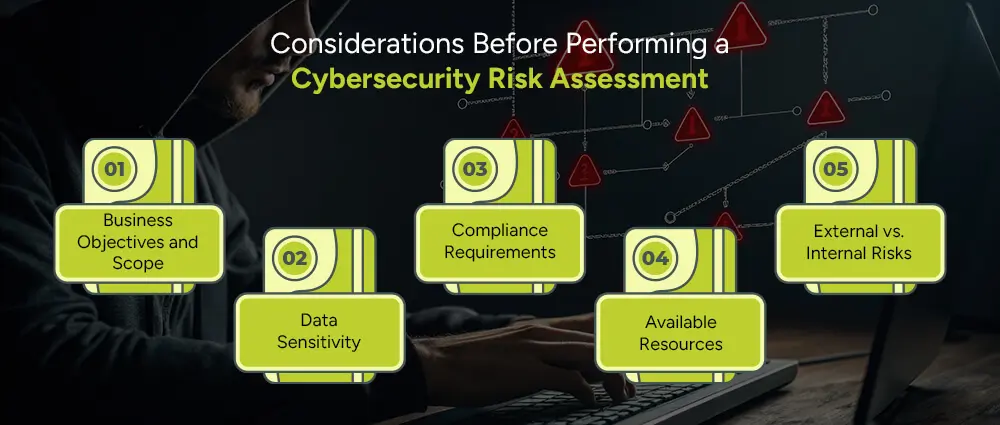
Before diving into a cybersecurity risk assessment, it’s important to pause and reflect on a few key things. This helps make sure your efforts are focused, effective, and aligned with your actual needs. Here are five important factors to think about:
Start by asking yourself: What are we trying to protect, and why?
Are you scanning the whole organization or just a particular part, like your finance department or customer service platform? A clear scope makes a great deal of difference. For example, if you wanted to protect customer data, your assessment would look something more like databases, CRM systems, and access control. However, if you intended to examine your entire business, your approach would have had to implicate a larger spectrum by department, from HR to IT. Think of it kind of like planning a road trip; You need to know your destination before you can even begin to map the route.
Not all data is created equal. Some information is much more sensitive than others, and understanding the different kinds of data that exist in your organization is critical to every risk assessment. This becomes even more critical when undertaking initiatives like Big Data Migration, where large volumes of data shift between environments.
Do you store customer credit card information? Employee medical records? or Confidential business strategies? The more sensitive the data, the more protection it needs. This will help you prioritize your security measures based on potential impact, what would hurt the most if it got into the wrong hands?
The regulations or standards that will be applicable to your business will depend heavily on the industry you’re in. These are not just things you need to live by; they are very much legal and operational must-haves. For instance, being in healthcare entails HIPAA compliances for patient health information. If you happen to be in finance, PCI-DSS may govern you in payment data or SOX in financial reporting. Any relevant regulations must be considered in a proper risk assessment to avoid facing fines or losing the trust of customers and stakeholders.
No organization can boast of having a bottomless well of money, time, or manpower. Therefore, it is strongly recommended that a realistic assessment of your reach be carried out.
Is this something that can be done internally, or will you need to outsource it? Do you have the right scanning tools for vulnerabilities or will you be investing in some? Some risk assessments are quick and high-level, while others are detailed and involve advanced technology. The resources you have available will therefore dictate which approach you follow.
Cyber threats may be from anywhere external or internal ones emanated by employee negligence, misuse of access, or even insider attacks: everything should be taking the same importance into consideration.
In fact, both should be taken into account in a comprehensive risk assessment. For example, do employees tend to use strong passwords? Access control is enabled so that unauthorized users cannot view sensitive information? Balancing internal and external threats creates a more holistic picture of your cybersecurity landscape.
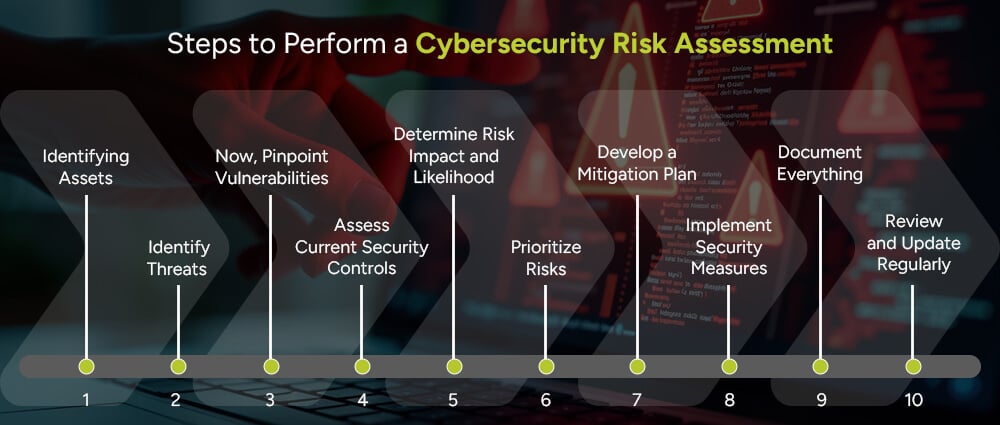
In large corporations, it is important that you know how to assess the environment of your system and see if your infrastructure is at risk. Here are a few simple steps that will help you identify, evaluate, and manage the threats to your digital systems:
Start by listing all your critical assets. This includes computers, servers, mobile devices, software applications, and sensitive data. Think about everything that plays a role in your day-to-day operations.
You can’t protect what you don’t know you have, so be thorough and organized here.
Next, ask yourself: What could go wrong? Threats can spring out of nowhere, could be anything from phishing emails and ransomware to natural disasters or insider mistakes. Don’t forget there’s always a risk of less obvious threats like stolen devices or social engineering.
One tip to follow in this scenario is to get creative, it will help you stay ahead of any malicious intrusions..
Now, look for weak points that make you more vulnerable to threats. This could entail outdated software, weak passwords, or a lack of employee security training.
Basically, any and everything that can be exploited by external factors needs to be on your radar.
Take stock of what protections you already have in place. firewalls, antivirus tools, access restrictions, etc.
Ask yourself: Are these controls working effectively? Are they up to date? Understanding what you’re already doing helps you see what gaps still need to be filled.
For each threat and vulnerability combo, think about how likely it is to happen and how bad the impact would be. Would it cause a minor inconvenience or bring your whole system down?
This helps you rank your risks from “nice to fix” to “must fix now.”
Now that you know the biggest risks, it’s time to prioritize. Start with those that are both highly likely and highly damaging. This way, you can use your time and resources where they matter most.
For each top-priority risk, create a step-by-step plan to reduce or eliminate it. This might include applying software patches, strengthening policies, getting a good cybersecurity patch management team, or rolling out staff training. Think practical, actionable, and tailored to your specific setup.
Put your mitigation strategies into action. Whether that’s configuring a firewall or training your team, execution is key. It is your duty to ensure that each action is tracked and completed thoroughly.
Keep detailed records of your risk assessment process, what you found, what you fixed, and what’s still pending. Documentation is essential for audits, compliance, and learning over time. It’s also helpful for onboarding new team members or when reviewing past issues.
Remember, Cyber threats aren’t a one-time thing. So, neither should your risk assessment be a once-in-a-lifetime thing. Set a schedule to review and refresh your process. Ideally, every 6 to 12 months or after major changes.
Staying proactive keeps your defenses strong and relevant.
Organizations that have achieved success with big data often emphasize cybersecurity assessments as a crucial part of their digital transformation journey.
Let’s say your company stores customer data in a cloud system. A risk assessment in cybersecurity would look something like this:
No organization is immune to cyber threats. But with the right cybersecurity risk assessment process, you can stay a few steps ahead of attackers. Whether you’re a large enterprise or a small startup, performing regular assessments is one of the smartest ways to secure your digital future.
Looking for help with this? Consider using trusted risk assessment services to guide you through the process and customize it to your needs.
A cybersecurity risk assessment checklist is a step-by-step guide that helps ensure all critical elements of the risk assessment process are covered. It typically includes:
Large organizations handle vast amounts of data, use complex systems, and have multiple entry points for attacks. A cyber risk assessment ensures they stay ahead of potential threats, avoid costly breaches, maintain trust, and meet compliance requirements.
Absolutely. Small businesses are often prime targets for cybercriminals because they may lack strong security controls. A basic risk assessment cybersecurity checklist can help small businesses protect sensitive data, stay compliant, and reduce the chances of cyberattacks, without breaking the bank.